Kaca Teknologi – A privilege escalation vulnerability was discovered in Google Search Console that allowed an attacker to export all performance data to BigQuery despite permission restrictions. This finding alone was rewarded with $3,133.70 through the Google Vulnerability Reward Program (VRP).
If you’re expecting a “fancy” exploitation scenario, this article may not meet your expectations.
Background of Discovering a Privilege Escalation Vulnerability in Google Search Console (GSC)
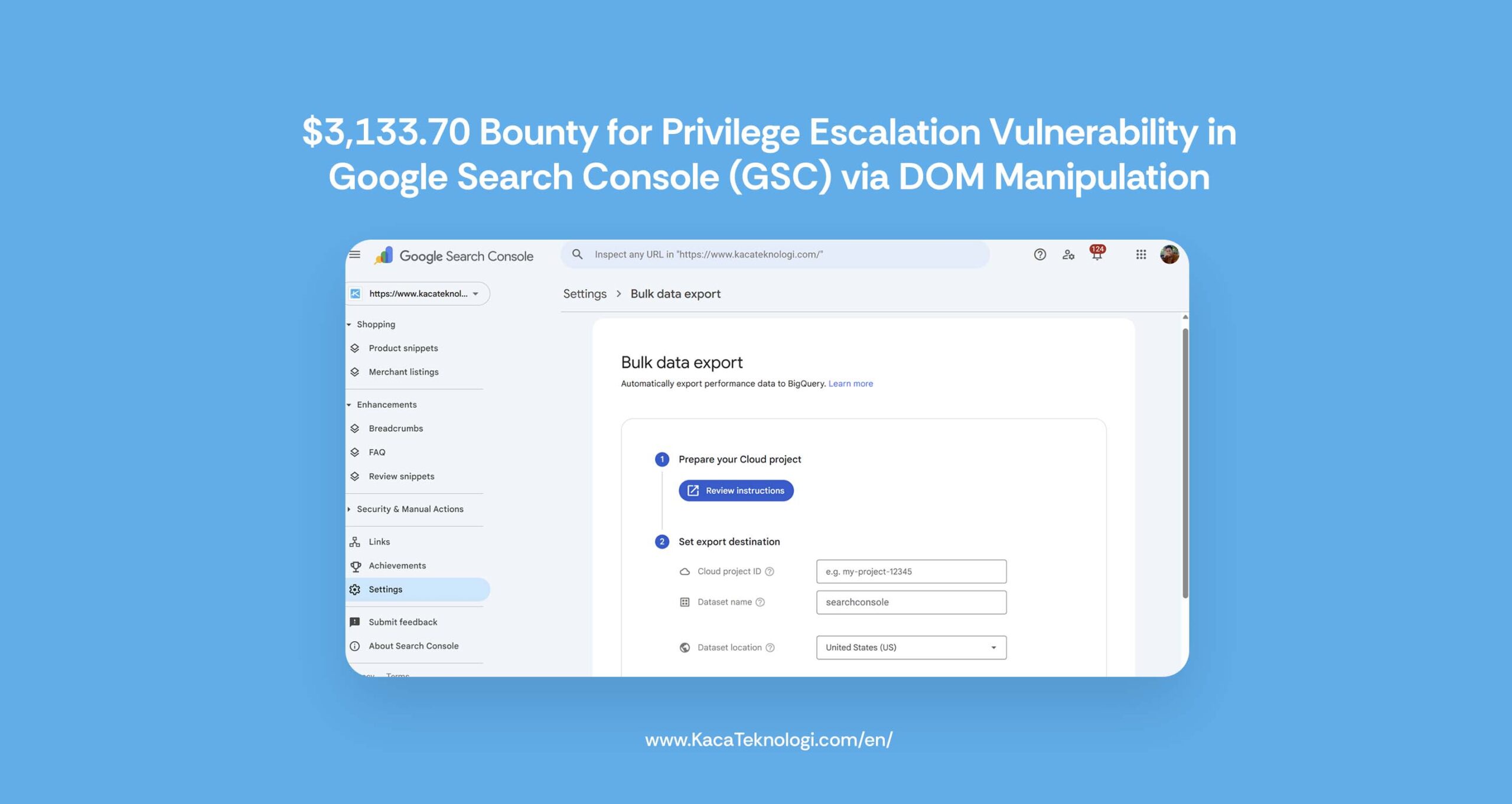
It all started at 2 AM when I needed to export my website performance data from GSC for data visualization. While looking for that feature, I came across the Bulk Data Export option to BigQuery.
The difference between exporting performance data to Google Sheets, CSV, or Excel is that those methods only allow a one-time export for the selected date. In contrast, Bulk Data Export provides full, unsampled datasets without the row limits of CSV exports, enabling automated daily transfers and long-term data retention.
However, when I tried to export the data, I encountered a message: “You must be a property owner.” The Continue button was disabled since my account only had a low-privilege role.
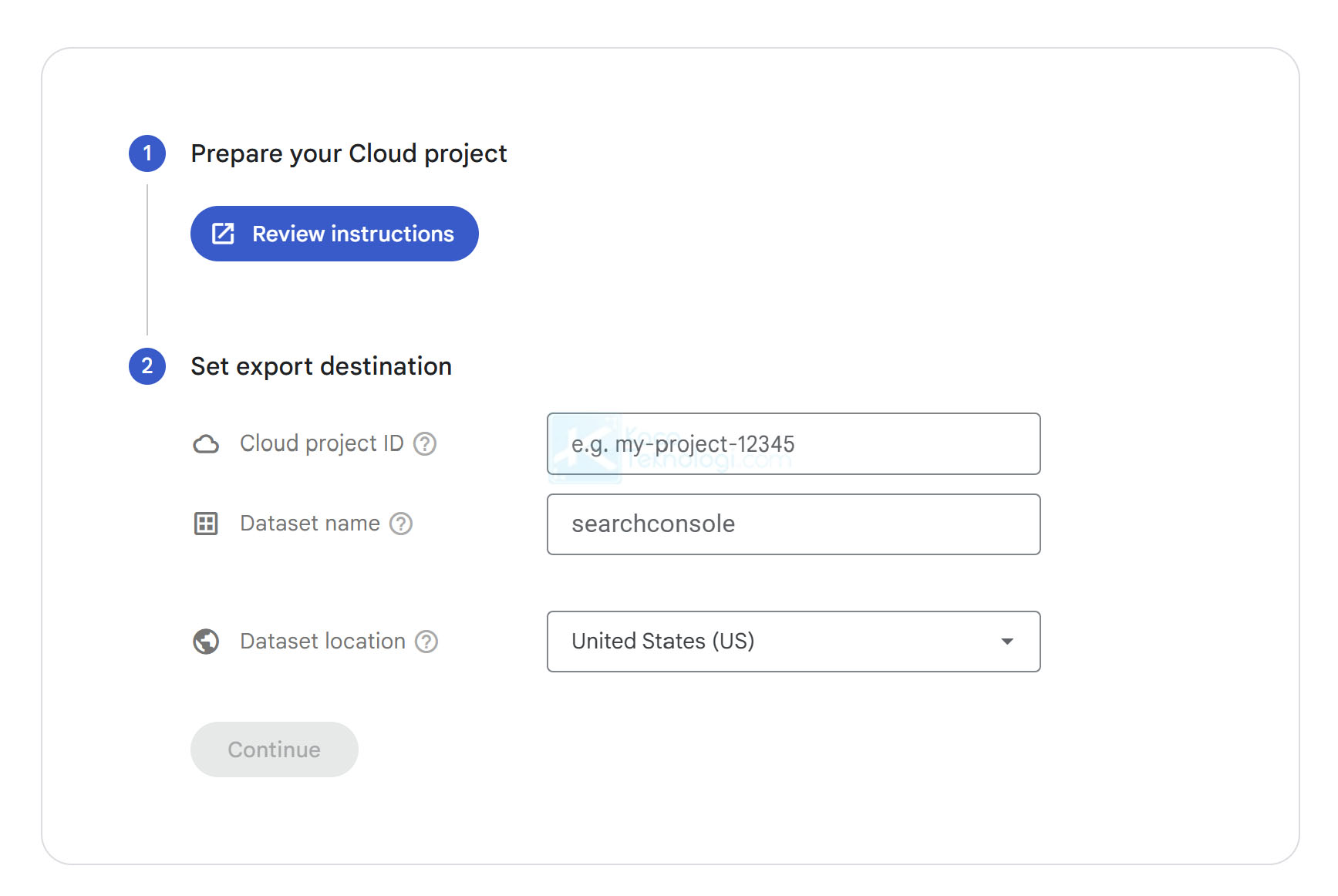
The word “must” indicates that the role of property owner is mandatory. Sometimes, when you’re looking for vulnerabilities and the documentation says “should”, you need to carefully validate whether the role is truly mandatory or if it’s still possible to perform certain actions through another endpoint or feature. Not every restriction that can be bypassed qualifies as a vulnerability.
I often attempt to bypass such restrictions, but I’ve learned that some are still considered intended behavior since they aren’t strictly mandatory. As a result, a few of my reports have been closed as informative.
Understanding The Roles in Google Search Console (GSC)
You may skip this part, but there’s a condition I want to emphasize. GSC has three main roles:
- Property Owner: full control over the property.
- Full User: can view site data and perform some actions.
- Restricted: can view site data but is limited in actions.
When testing Broken Access Control (BAC), usually each role behaves differently. If a restriction cannot be bypassed in role A, that doesn’t mean it’s not bypassable in role B, so test each role.
I usually apply a “what-if approach” to explore and attempt exploits for every role; this helps me craft dozens of exploitation scenarios. I’ll discuss this more deeply in another article.
Bypassing the Restriction to Fully Export Performance Data
Since it was 2 AM and I was too lazy to open Burp Suite, whether I used Burp or not didn’t matter as long as I achieved the goal.
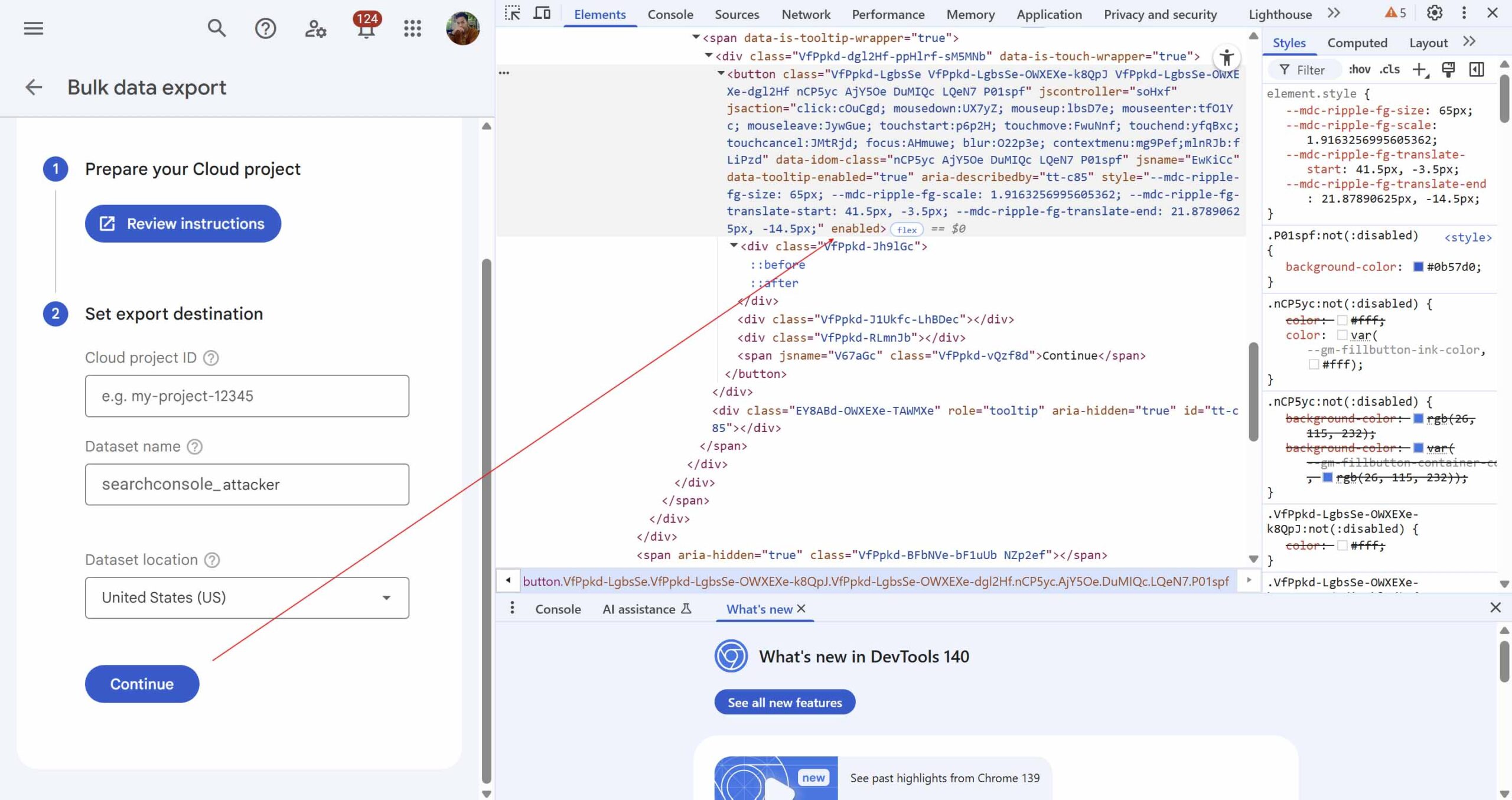
Using a Full role, I configured my Google Cloud project and then right-clicked the disabled Continue button in the UI. I modified the button element from disabled to enabled, which made the Continue button clickable.
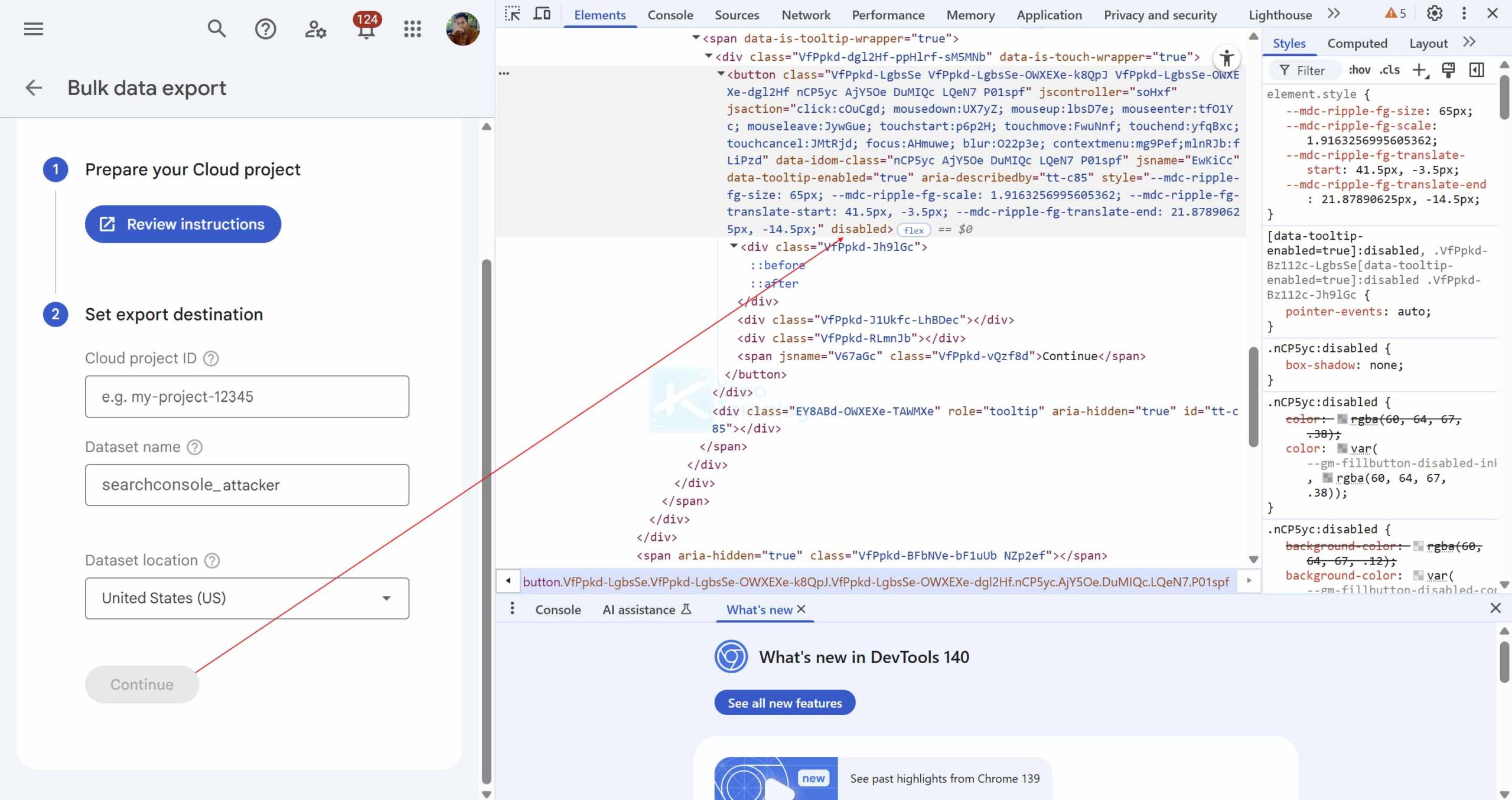
Here is the complete code before modification:
<button class="VfPpkd-LgbsSe VfPpkd-LgbsSe-OWXEXe-k8QpJ VfPpkd-LgbsSe-OWXEXe-dgl2Hf nCP5yc AjY5Oe DuMIQc LQeN7 P01spf" jscontroller="soHxf" jsaction="click:cOuCgd; mousedown:UX7yZ; mouseup:lbsD7e; mouseenter:tfO1Yc; mouseleave:JywGue; touchstart:p6p2H; touchmove:FwuNnf; touchend:yfqBxc; touchcancel:JMtRjd; focus:AHmuwe; blur:O22p3e; contextmenu:mg9Pef;mlnRJb:fLiPzd" data-idom-class="nCP5yc AjY5Oe DuMIQc LQeN7 P01spf" jsname="EwKiCc" data-tooltip-enabled="true" aria-describedby="tt-c85" style="--mdc-ripple-fg-size: 65px; --mdc-ripple-fg-scale: 1.9163256995605362; --mdc-ripple-fg-translate-start: 41.5px, -3.5px; --mdc-ripple-fg-translate-end: 21.87890625px, -14.5px;" disabled=""><div class="VfPpkd-Jh9lGc"></div><div class="VfPpkd-J1Ukfc-LhBDec"></div><div class="VfPpkd-RLmnJb"></div><span jsname="V67aGc" class="VfPpkd-vQzf8d">Continue</span></button>The code after modification:
<button class="VfPpkd-LgbsSe VfPpkd-LgbsSe-OWXEXe-k8QpJ VfPpkd-LgbsSe-OWXEXe-dgl2Hf nCP5yc AjY5Oe DuMIQc LQeN7 P01spf" jscontroller="soHxf" jsaction="click:cOuCgd; mousedown:UX7yZ; mouseup:lbsD7e; mouseenter:tfO1Yc; mouseleave:JywGue; touchstart:p6p2H; touchmove:FwuNnf; touchend:yfqBxc; touchcancel:JMtRjd; focus:AHmuwe; blur:O22p3e; contextmenu:mg9Pef;mlnRJb:fLiPzd" data-idom-class="nCP5yc AjY5Oe DuMIQc LQeN7 P01spf" jsname="EwKiCc" data-tooltip-enabled="true" aria-describedby="tt-c85" style="--mdc-ripple-fg-size: 65px; --mdc-ripple-fg-scale: 1.9163256995605362; --mdc-ripple-fg-translate-start: 41.5px, -3.5px; --mdc-ripple-fg-translate-end: 21.87890625px, -14.5px;" enabled=""><div class="VfPpkd-Jh9lGc"></div><div class="VfPpkd-J1Ukfc-LhBDec"></div><div class="VfPpkd-RLmnJb"></div><span jsname="V67aGc" class="VfPpkd-vQzf8d">Continue</span></button>After modifying the button, the export action succeeded and I was able to export Search Console performance data to my Google Cloud project despite not having the required property owner permission. Once the export started, the attacker could not stop the export process. I repeated the same DOM modification to enable and then stop the export process.
For clarity, see the video PoC below.
I reported the vulnerability to Google VRP and within two weeks I received a bounty of $3,133.70 for this finding.

Report Timeline
- Reported: Aug 11, 2025 | 03:43
- Received comment: Aug 12, 2025 | 07:05 — “This report seems to describe an issue in Google Cloud.”
- Triaged: Aug 12, 2025 | 23:30
- Accepted: Aug 15, 2025 | 07:04
- Rewarded: Aug 26, 2025 | 20:56 — $3,133.70 (downgrade applied because the attacker needed access to an impacted victim’s project; otherwise the reward could have been $5,000)
- Fixed: Sep 05, 2025 | 06:26
- Retested / Confirmed non-reproducible: Sep 05, 2025 | 08:54
Conclusion
Whether you need a fancy or simple exploit, use advanced tools or just Inspect Element, or work on a high-spec or low-end laptop, tools are just tools. They help, but relying on them too much misses the point: some vulnerabilities can also be discovered and exploited with very simple techniques.
FYI, I save time when DOM manipulation is enough to exploit an issue. Still, $3K is $3K for a straightforward vulnerability.

aihhh mantapp bang.
terima kasih sudah berbagi